Table of contents
- What is the 3-2-1 backup rule?
- Why the 3-2-1 rule is essential for Business Continuity
- How the 3-2-1 backup strategy works: key aspects every business should know
- Step-by-step guide to implementing the 3-2-1 rule
- Common mistakes companies make when applying the 3-2-1 rule
- Types of storage suitable for the 3-2-1 backup method
- Modern approaches: 3-2-1-1-0 and 4-3-2 explained
- Conclusion: a proven strategy supported by Hystax Acura
Losing business-critical information due to human error, cyberattacks, or infrastructure failures remains one of the most costly operational risks today. A simple, time-tested way to reduce this risk is the 3-2-1 backup rule, a backup strategy that boils down to this: your data protection approach must rely on three copies, different media, and at least one stored offsite.
Despite its age, this rule still outperforms many newer approaches because it is straightforward, adaptable, and aligned with modern backup strategies used in hybrid and multi-cloud environments.
Below, we break down what the 3-2-1 rule means, why it matters, how to implement it, and where companies often make mistakes. The article also explores modern changes or variations, as well as the storage types that make this strategy effective for real-world business needs.
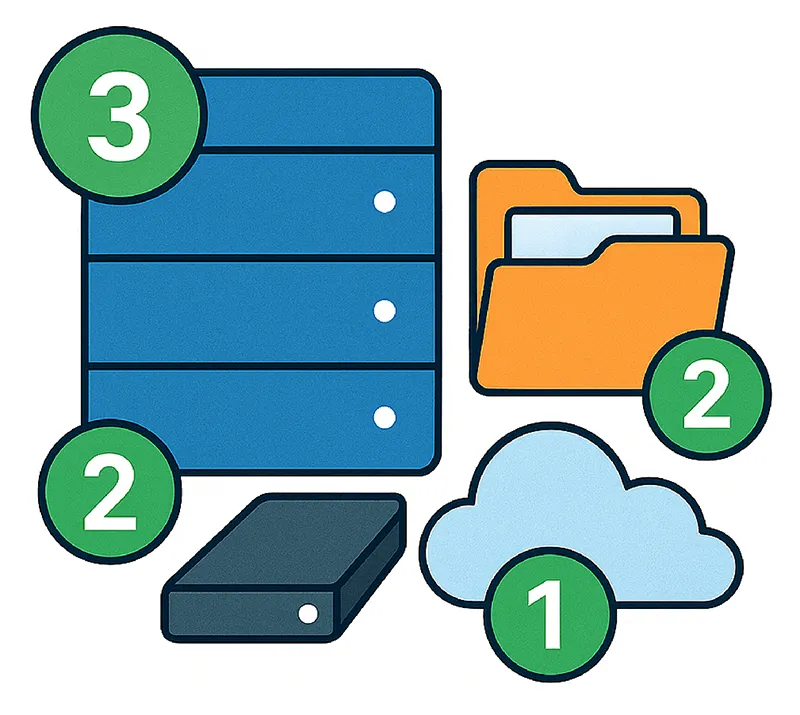
What is the 3-2-1 backup rule?
The 3-2-1 backup rule means you maintain:
- 3 total copies of your data (one primary and two backups),
- stored on two different media types,
- with one copy stored offsite.
This approach ensures that even if one system fails or one media type becomes corrupted, your data backup remains available. It is a foundational 3-2-1 backup strategy recommended by cybersecurity experts, compliance standards, and IT leaders.
Why the 3-2-1 rule is essential for Business Continuity
No organization is immune to disruptions. Implementing the 3-2-1 backup method significantly reduces the risk of data loss by creating redundancy across multiple storage layers.
Key risks it helps prevent include:
Ransomware attacks
Modern ransomware encrypts not only production systems but also accessible backups. Offsite and offline copies help maintain clean recovery points.
Infrastructure failures
Integrate object storage databases across different providers for improved data protection and resilience. This model allows businesses to combine cloud object scalability with on-premises security, supporting distributed cloud strategies and enabling seamless storage use across various environments.
Human error
Accidental deletions or misconfigurations happen daily. Three copies guarantee recoverability from user mistakes.
Natural disasters or regional outages
Keeping at least one backup off-site protects against regional events such as fire, flood, or a cloud provider’s incident.
Compliance and SLA requirements
Many industries require proven protection strategies to meet compliance rules and internal SLAs on availability, backups, and data retention.
The 1-2-3 backup strategy is simple, but its business impact is profound: fewer operational disruptions, predictable recovery, and stronger customer trust.
How the 3-2-1 backup strategy works: key aspects every business should know
To make the 3-2-1 backup strategy reliable, companies must look beyond the numbers and consider several practical requirements:
1. Three copies: not just duplication, but diversification
The primary dataset, plus at least two backups, allows you to maintain recovery options even when corruption goes unnoticed for days.
2. Two different storage media types
The idea behind different media is resilience: block volumes + object storage, disk + tape, on-prem storage + cloud bucket, etc. Using identical media types across all layers creates avoidable single-point failures.
3. One off-site or cloud copy
This stored-offsite component is essential for true data protection. It ensures continuity even if your entire facility becomes inaccessible.
4. Respecting retention policies and recovery objectives
Set backup frequency based on RPO/RTO targets so backups truly support your operational recovery needs.
5. Validating integrity and testing recovery
A backup is only valuable when it can be restored. Periodic validation eliminates unpleasant surprises during emergencies.
Together, these components turn the 3-2-1 backup methodology into a practical, repeatable strategy rather than a theoretical guideline.
Step-by-step guide to implementing the 3-2-1 rule
Below is a clear, actionable implementation plan suitable for SMBs and large enterprises alike.
1. Define the scope of what must be protected
Identify workloads, applications, databases, and files requiring consistent backups. Prioritize systems with strict SLA requirements or high operational value.
2. Choose at least two storage types
Select complementary storage technologies — e.g., local block storage + S3 object storage. This ensures your data backup remains resilient across different infrastructure layers.
3. Create and automate full backups
A full backup should be performed at least once per week for most environments, depending on your data-change rate. Underestimating the frequency of full snapshots is one of the biggest operational gaps companies face.
4. Add incremental backups to reduce overhead
Daily or hourly incremental backups minimize load on your systems while maintaining the three-copy rule.
5. Keep one secure off-site copy
A cloud repository or a secondary data center enables rapid failover in emergencies. This also satisfies compliance requirements tied to data protection and long-term retention.
6. Encrypt and monitor backups
Security controls prevent tampering and ensure that backup media cannot be exploited if compromised.
7. Test your restore process
A backup strategy without recovery testing is incomplete. A quarterly recovery simulation ensures that your 321 backup method works during a real outage.
Following these steps transforms the 3-2-1 data backup strategy into an operationally sound, test-driven safeguard.
Common mistakes companies make when applying the 3-2-1 rule
Even though the rule is straightforward, many companies misapply it. The most frequent issues include:
Relying only on on-site backups
Local backups stored on the same infrastructure do not protect against disasters or site-wide failures.
Skipping offsite storage entirely
Without a remote copy, the strategy loses its core advantage — geographical diversification.
Not performing full backups regularly
A too-long interval between full backups slows recovery and increases the risk of data loss. Weekly full backups remain best practice for most organizations.
Mixing up media types but storing them together
Different media types stored in the same rack still introduce the same physical-location risk.
No monitoring or testing of backups
Backups may silently fail due to network, quota, or software issues. Regular restore tests verify integrity and performance.
Treating backup as a one-time setup
A backup strategy must be continuously maintained to reflect infrastructure changes, new workloads, and updated SLAs.
Avoiding these mistakes increases the reliability of your 321 data backup approach and reduces long-term operational risks.
Types of storage suitable for the 3-2-1 backup method
The 3-2-1 backup strategy works with many technologies. The most common storage options include:
External hard drives and NAS
Useful for on-prem environments, though vulnerable to physical damage.
Cloud object storage (e.g., S3, Azure Blob, Google Cloud Storage)
Highly durable, scalable, and suitable for off-site requirements.
Tape libraries
Still relevant for long-term archival and offline retention.
Dedicated backup appliances
Provide integrated hardware + software optimized for continuous replication.
Hybrid local + cloud repositories
A balanced approach for businesses needing fast local recovery and cloud-level safety.
Combining two or more of these ensures compliance with the rule’s requirement for different media types.
Modern approaches: 3-2-1-1-0 and 4-3-2 explained
As threats evolve, IT teams extend the classic rule into advanced models:
3-2-1-1-0
An additional offline or immutable copy, plus zero errors verified through regular testing, ensures backup integrity and strengthens ransomware resilience. This approach helps protect recovery points from tampering or encryption and ensures that at least one clean backup remains accessible even if primary or secondary copies become compromised.
4-3-2
Four total copies across three different media and two off-site locations create a highly resilient backup structure suitable for organizations with demanding continuity and compliance requirements. By diversifying storage platforms and geographic locations, the 4-3-2 approach minimizes systemic failure risks and enables rapid recovery even during large-scale cloud outages or regional disruptions.
These backup variations or changes are not replacements but enhancements to the original 3-2-1 backup methodology, especially in complex cloud or hybrid infrastructures.
See how Hystax Acura implements the 3-2-1 rule and Double Storage to ensure uninterrupted data resilience.
Thank you for your request!
We will be in touch soon.
Conclusion: a proven strategy supported by Hystax Acura
The 3-2-1 backup rule remains one of the most reliable ways to secure business-critical information, reduce the risk of data loss, and build long-term operational resilience. When combined with automation, testing, and secure storage, it becomes a robust foundation for modern backup strategies.
Hystax Acura helps companies follow this principle effortlessly thanks to features such as Double Storage, agentless replication, and automated backup policy management. With Hystax, you can implement the 321 backup approach consistently across hybrid and multi-cloud environments — ensuring that your three copies are always protected, verified, and ready for fast recovery.