Recently companies are increasingly aware of the need to overcome challenges with access management mechanisms as one of the most important issues of companies’ IT security. The list of security threats, which are crucial for businesses and lead to production stoppage, is long, and a significant number of successful cyberattacks on an organization’s IT infrastructure and data are caused by weaknesses in access management to internal workloads and environments of the company.

The need for robust workloads access management has become a central asset of an enterprise IT landscape. A holistic access management strategy enables companies to meet security standards, improve employee productivity with a streamlined authentication procedure and reduce the risk of attacks and data breaches.
Enterprises, SMBs and start-ups are challenged with providing temporary access to internal environments.
Core challenges of secure access management for company environments
1. The same credentials for all environments
The majority of companies have issues with providing their employees with secure temporary and revocable access to internal resources of the organization. It is a common case when all engineers, DevOps engineers or QA specialists are granted the same credentials with equal user rights to access all environments and those credentials are never revoked. It obviously can damage IT security.
2. The complexity of the process of granting and revoking access
Security specialists should assign individual permissions, privileges, access groups and authorization roles for all users, keep them up to date and regularly change regarding security recommendations. The flow usually consists of onboarding new users, granting roles or permissions, and removing users. The complexity of the process leads to a situation when employees have issues with the access to necessary environments, ex-employees can still access internal corporate resources, the company loses control over privileged access and gets productivity and security troubles.
3. A lack of a centralized and automated access management solution
Without a centralized and automated solution, IT staff provision all access rights and roles manually. In practice such manual mechanisms are incredibly inefficient, can cause human errors and don’t scale well for companies with hundreds of engineers.
The increasing number of environments and employees constantly enhances the complexity of authentication and access mechanisms for companies that do not have a strong and comprehensive approach to an access management strategy.
A secure access management approach with OptScale
A great number of companies today face the challenges mentioned above. OptScale was designed to bolster access management security issues with a simple and automated flow of granting and revoking individual access to IT environments.
By invoking a job, script or webhook that generates a temporary password or providing a pub key only for a unique working session, OptScale gives an opportunity to avoid sharing a standard password and get rid of uncontrolled and irrevocable access to internal resources.
Traditional environment access management flow

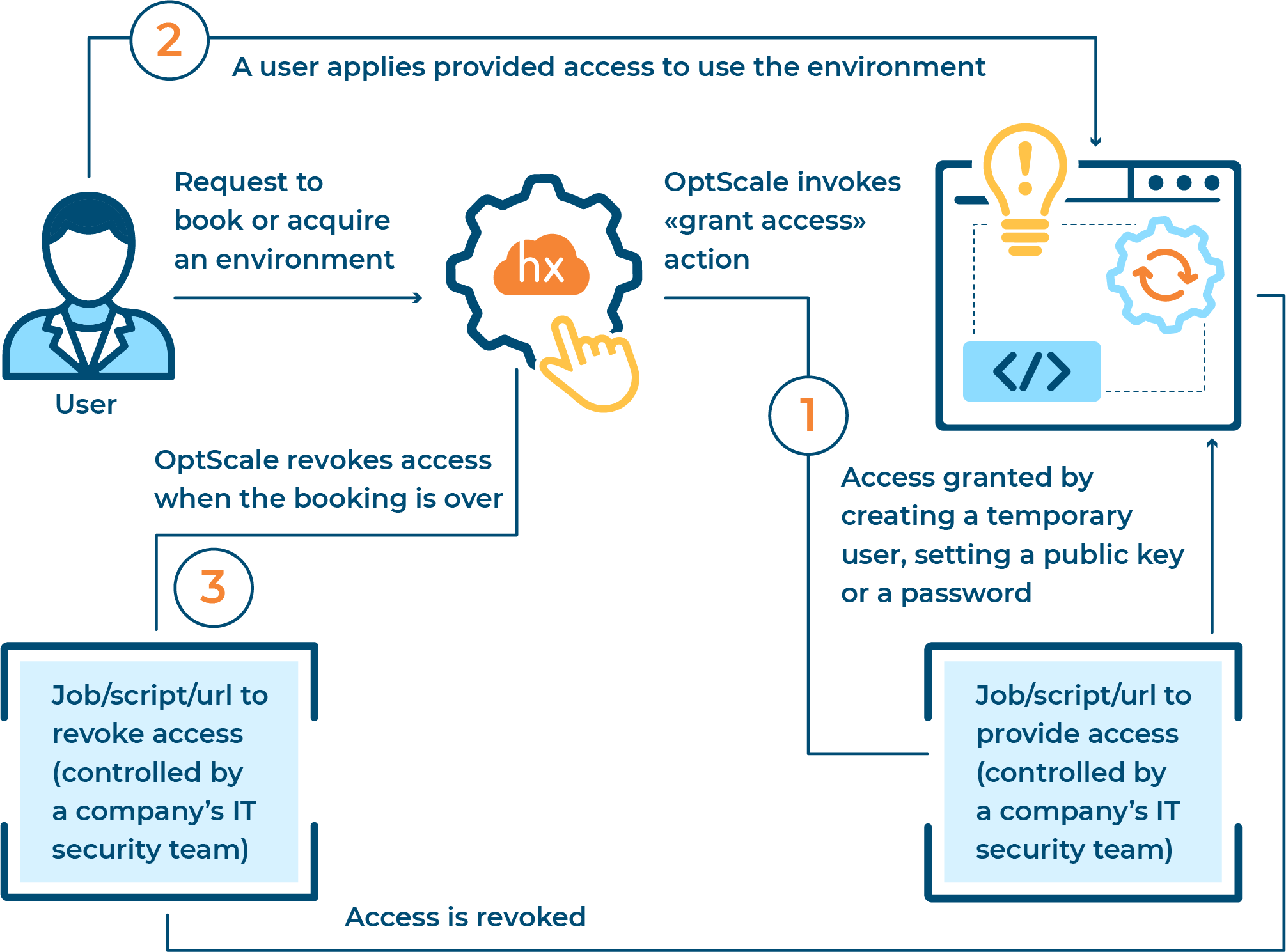
Environment access flow with OptScale in 3 steps
Step 1
A user’s requests to acquire or book an environment from a list of company’s resources. OptScale invokes a jobs/scripts/url to provide an access, which is granted by creating a temporary user, setting a pub key or a password.
Jobs with open-source samples are considered as a black box system for OptScale and fully controlled by the security teams of a company. This procedure enables a company to build a secure mechanism of generating authentication data without getting access to the internal process of the company’s access management.
Step 2
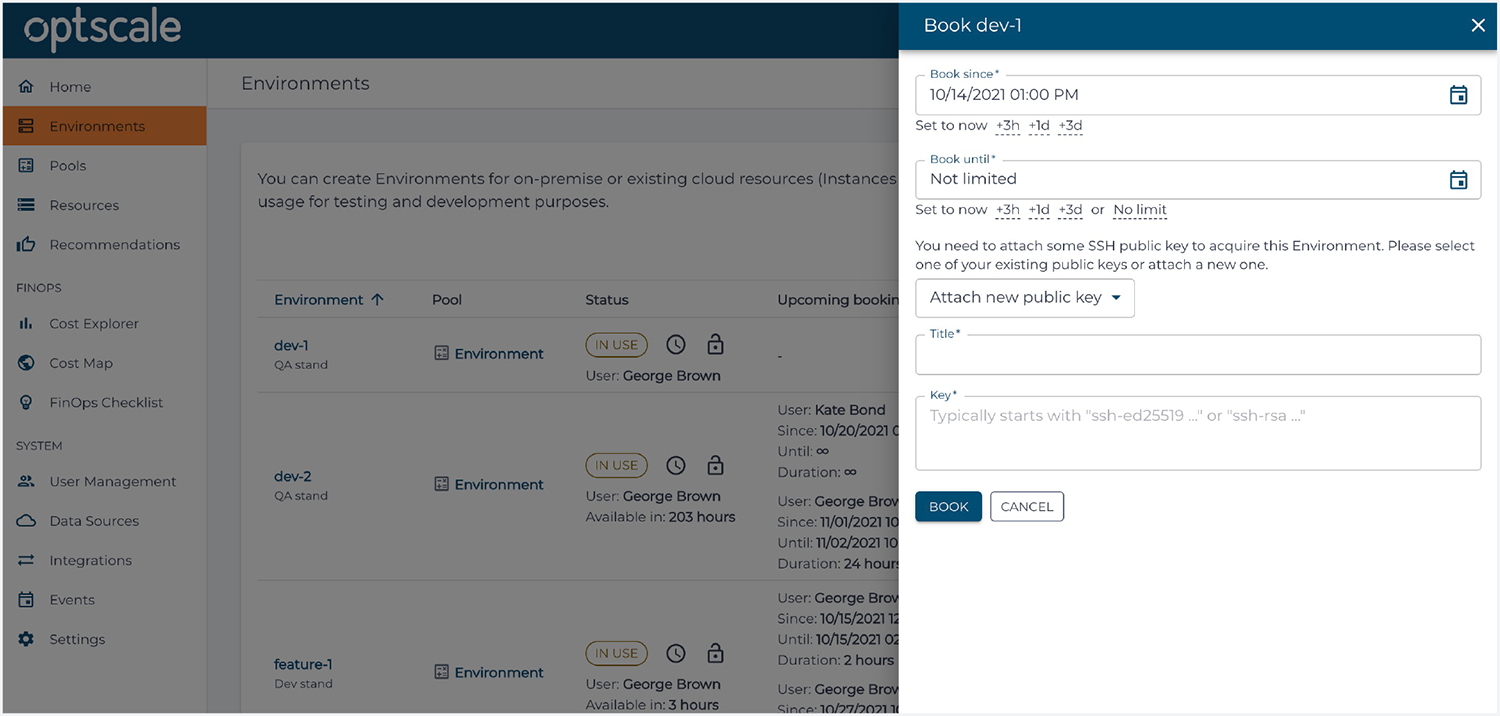
Since a user has been invited within an organization in OptScale and has been assigned an ‘Engineer’ role, he or she gets an opportunity to schedule the use of environments. With OptScale companies are able to manage access to internal and production environments securely by granting individual credentials for every work session.
Step 3
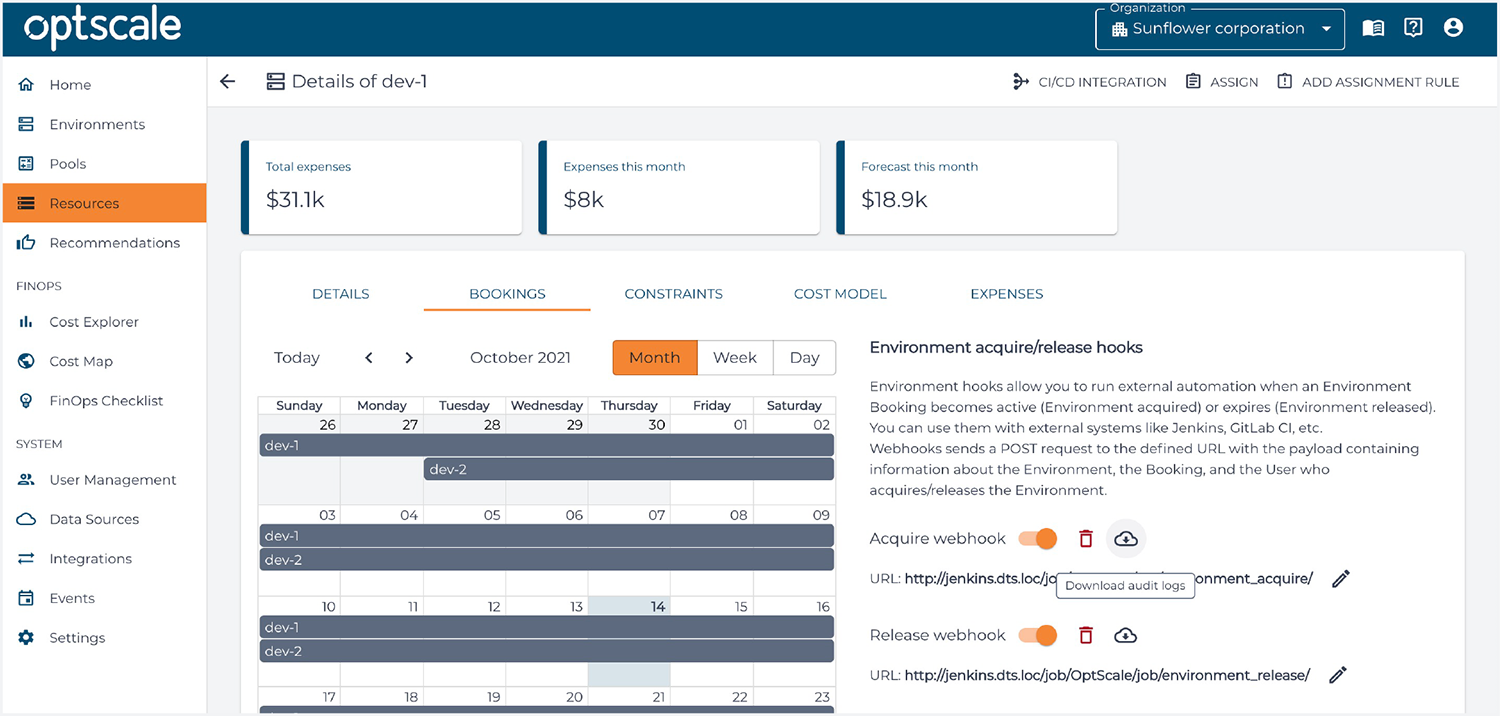
OptScale automatically revokes access, when the booking is over or the environment is released. After a work session an environment manager can review environment access audit logs and get all the necessary details like who and when used the environment and other technical details.
Final thought
Company’s security departments face the increasingly complex challenge of providing secure access management to IT environments, avoiding uncontrolled usage of your internal resources and restricting unauthorized access to critical systems. A solid workload access management solution goes a long way in automating daily tasks of DevSecOps and IT security teams, mitigating risks and implementing IT security best practices at your company.
Register here to start environment access management with OptScale → https://my.optscale.com/register