En los últimos tiempos, las empresas son cada vez más conscientes de la necesidad de superar los desafíos de los mecanismos de gestión de acceso como uno de los problemas más importantes de la seguridad informática de las empresas. La lista de amenazas a la seguridad, que son cruciales para las empresas y conducen a la interrupción de la producción, es larga y un número significativo de Ciberataques exitosos Los problemas en la infraestructura de TI y los datos de una organización son causados por debilidades en la gestión del acceso a las cargas de trabajo y entornos internos de la empresa.

La necesidad de una gestión robusta del acceso a las cargas de trabajo se ha convertido en un activo central del panorama de TI empresarial. Una estrategia integral de gestión de acceso permite a las empresas cumplir con los estándares de seguridad, mejorar la productividad de los empleados con un procedimiento de autenticación optimizado y reducir el riesgo de ataques y violaciones de datos.
Las empresas, pymes y empresas emergentes se enfrentan al desafío de proporcionar acceso temporal a entornos internos.
Principales desafíos de la gestión de acceso seguro para entornos empresariales
1. Las mismas credenciales para todos los entornos
La mayoría de las empresas tienen problemas para proporcionar a sus empleados acceso temporal y revocable seguro a los recursos internos de la organización. Es un caso común cuando a todos los ingenieros, ingenieros de DevOps o especialistas de control de calidad se les otorgan las mismas credenciales con los mismos derechos de usuario para acceder a todos los entornos. y esas credenciales nunca se revocanObviamente puede dañar la seguridad informática.
2. La complejidad del proceso de concesión y revocación del acceso
Los especialistas en seguridad deben asignar permisos individuales, privilegios, grupos de acceso y roles de autorización para todos los usuarios, mantenerlos actualizados y modificarlos periódicamente en función de las recomendaciones de seguridad. El flujo suele consistir en incorporar nuevos usuarios, otorgar roles o permisos y eliminar usuarios. La complejidad del proceso lleva a una situación en la que los empleados tienen problemas con el acceso a los entornos necesarios, los ex empleados aún pueden acceder a los recursos corporativos internos, la empresa pierde el control sobre el acceso privilegiado y surgen problemas de productividad y seguridad.
3. Falta de una solución de gestión de acceso centralizada y automatizada
Sin una solución centralizada y automatizada, el personal de TI asigna todos los derechos y roles de acceso de forma manual. En la práctica, estos mecanismos manuales son increíblemente ineficientes, pueden provocar errores humanos y no son adecuados para empresas con cientos de ingenieros.
El creciente número de entornos y empleados aumenta constantemente la complejidad de los mecanismos de autenticación y acceso para las empresas que no cuentan con un enfoque sólido e integral para una estrategia de gestión de acceso.
Un enfoque de gestión de acceso seguro con OptScale
Un gran número de empresas se enfrentan hoy en día a los retos mencionados anteriormente. OptScale Fue diseñado para reforzar los problemas de seguridad en la gestión de acceso con un flujo simple y automatizado de concesión y revocación de acceso individual a entornos de TI.
Al invocar un trabajo, un script o un webhook que genere una contraseña temporal o proporcione una clave pública solo para una sesión de trabajo única, OptScale brinda la oportunidad de evitar compartir una contraseña estándar y deshacerse del acceso no controlado e irrevocable a los recursos internos.
Flujo de gestión de acceso al entorno tradicional

Flujo de acceso al entorno con OptScale en 3 pasos
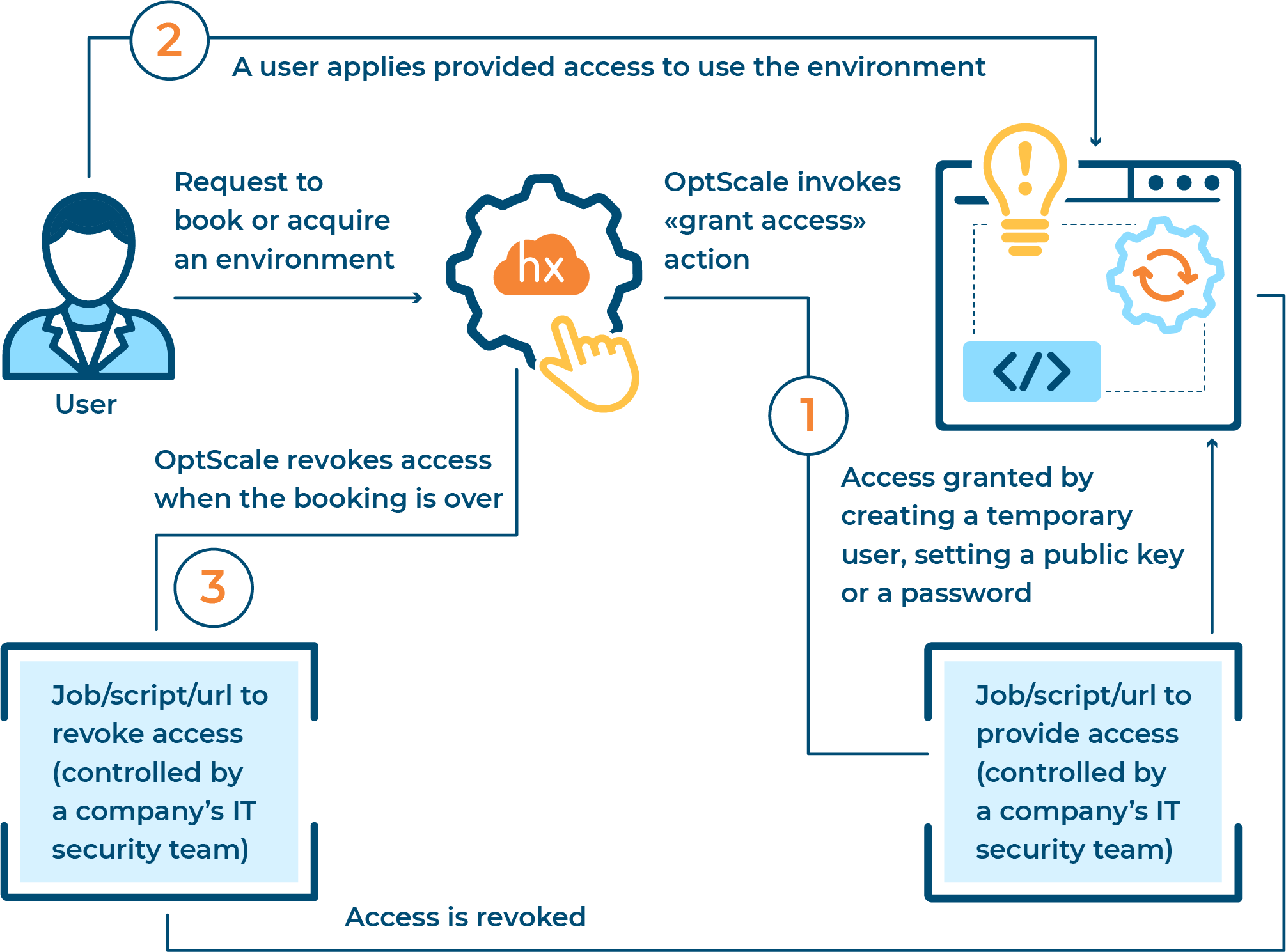
Paso 1
Solicitudes de un usuario para adquirir o reservar un entorno de una lista de recursos de la empresa. OptScale invoca un trabajo/script/URL para proporcionar acceso, que se concede creando un usuario temporal, configurando una clave pública o una contraseña.
Los trabajos con muestras de código abierto se consideran un sistema de caja negra para OptScale y están totalmente controlados por los equipos de seguridad de una empresa. Este procedimiento permite a una empresa crear un mecanismo seguro para generar datos de autenticación sin tener acceso al proceso interno de gestión de acceso de la empresa.
Paso 2
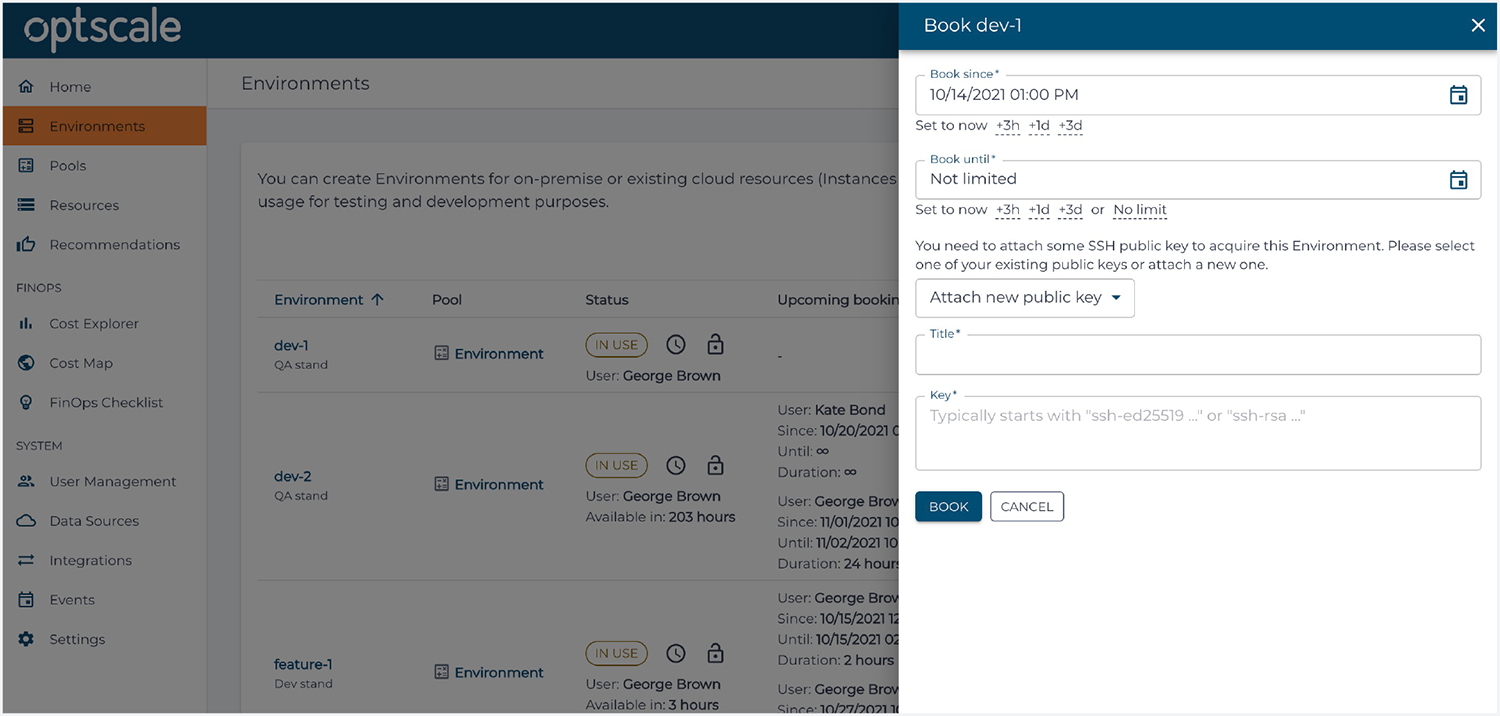
Dado que un usuario ha sido invitado a una organización en OptScale y se le ha asignado un rol de "Ingeniero", tiene la oportunidad de programar el uso de los entornos. Con OptScale, las empresas pueden gestionar el acceso a los entornos internos y de producción de forma segura otorgando credenciales individuales para cada sesión de trabajo.
Paso 3
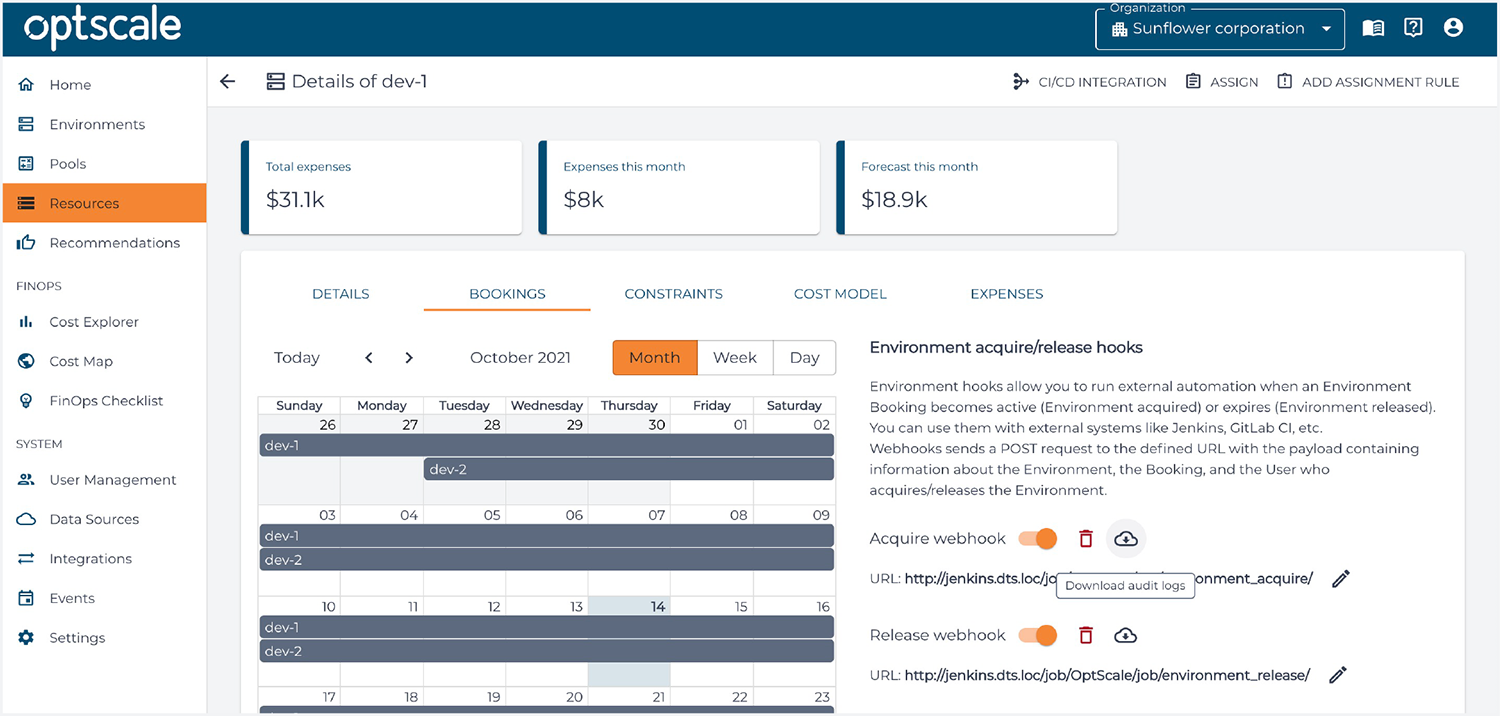
OptScale revoca automáticamente el acceso cuando finaliza la reserva o se libera el entorno. Después de una sesión de trabajo, un administrador del entorno puede revisar los registros de auditoría de acceso al entorno y obtener todos los detalles necesarios, como quién y cuándo utilizó el entorno y otros detalles técnicos.
Pensamiento final
Los departamentos de seguridad de las empresas se enfrentan al reto cada vez más complejo de proporcionar una gestión de acceso seguro a los entornos de TI, evitando el uso descontrolado de sus recursos internos y restringiendo el acceso no autorizado a los sistemas críticos. Una carga de trabajo sólida Solución de gestión de acceso Contribuye en gran medida a automatizar las tareas diarias de los equipos de DevSecOps y seguridad de TI, mitigando riesgos e implementando las mejores prácticas de seguridad de TI en su empresa.
Regístrese aquí para comenzar a gestionar el acceso al entorno con OptScale → https://my.optscale.com/register