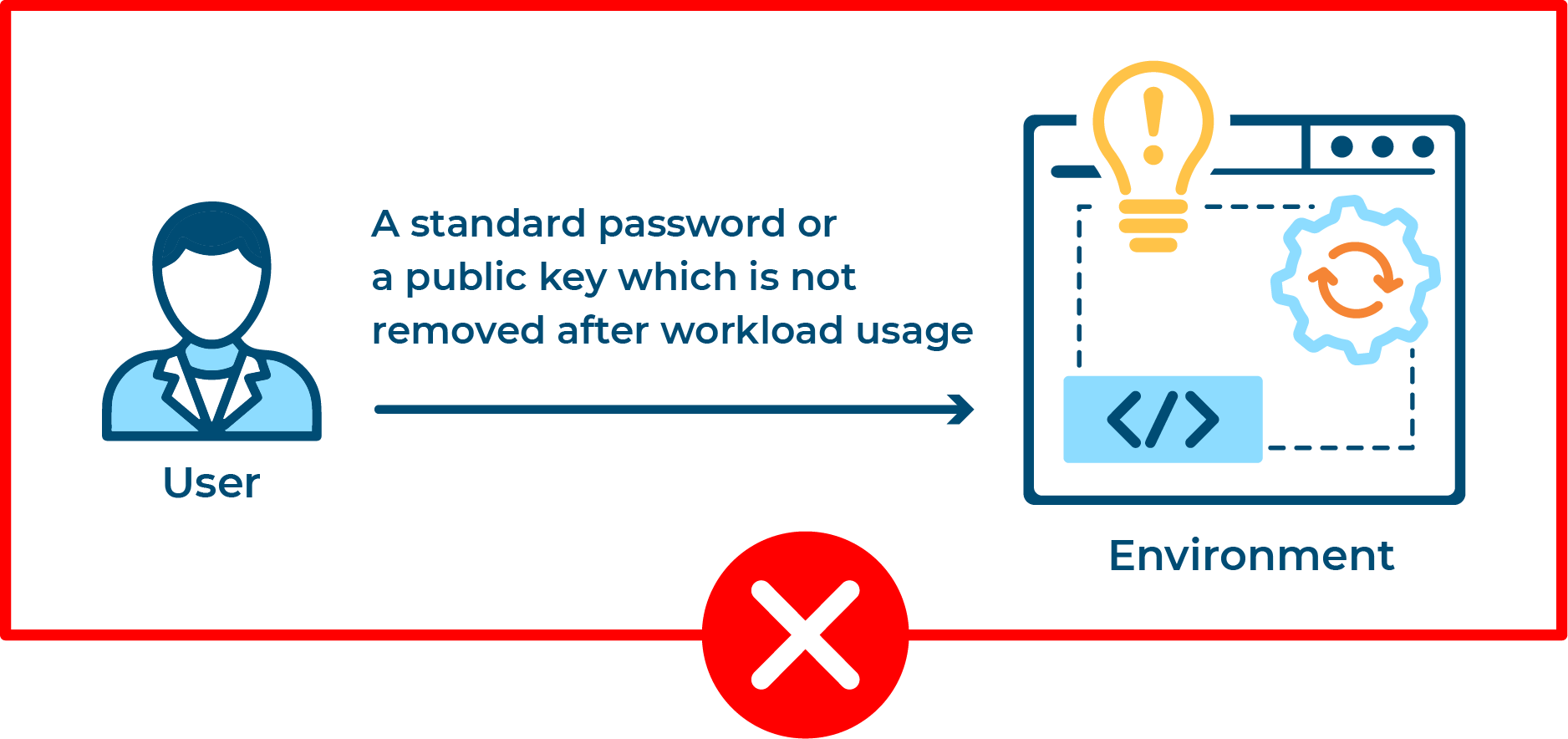
Whitepaper 'FinOps y gestión de costes para Kubernetes'
Considere darle a OptScale unEstrella en GitHub, es 100% de código abierto. Aumentaría su visibilidad ante los demás y aceleraría el desarrollo de productos. ¡Gracias!
Únase a nosotros en un seminario web:Migración de VMware a escala: cómo trasladar miles de máquinas virtuales con una interrupción mínima
Ebook 'De FinOps a estrategias comprobadas de gestión y optimización de costos en la nube'
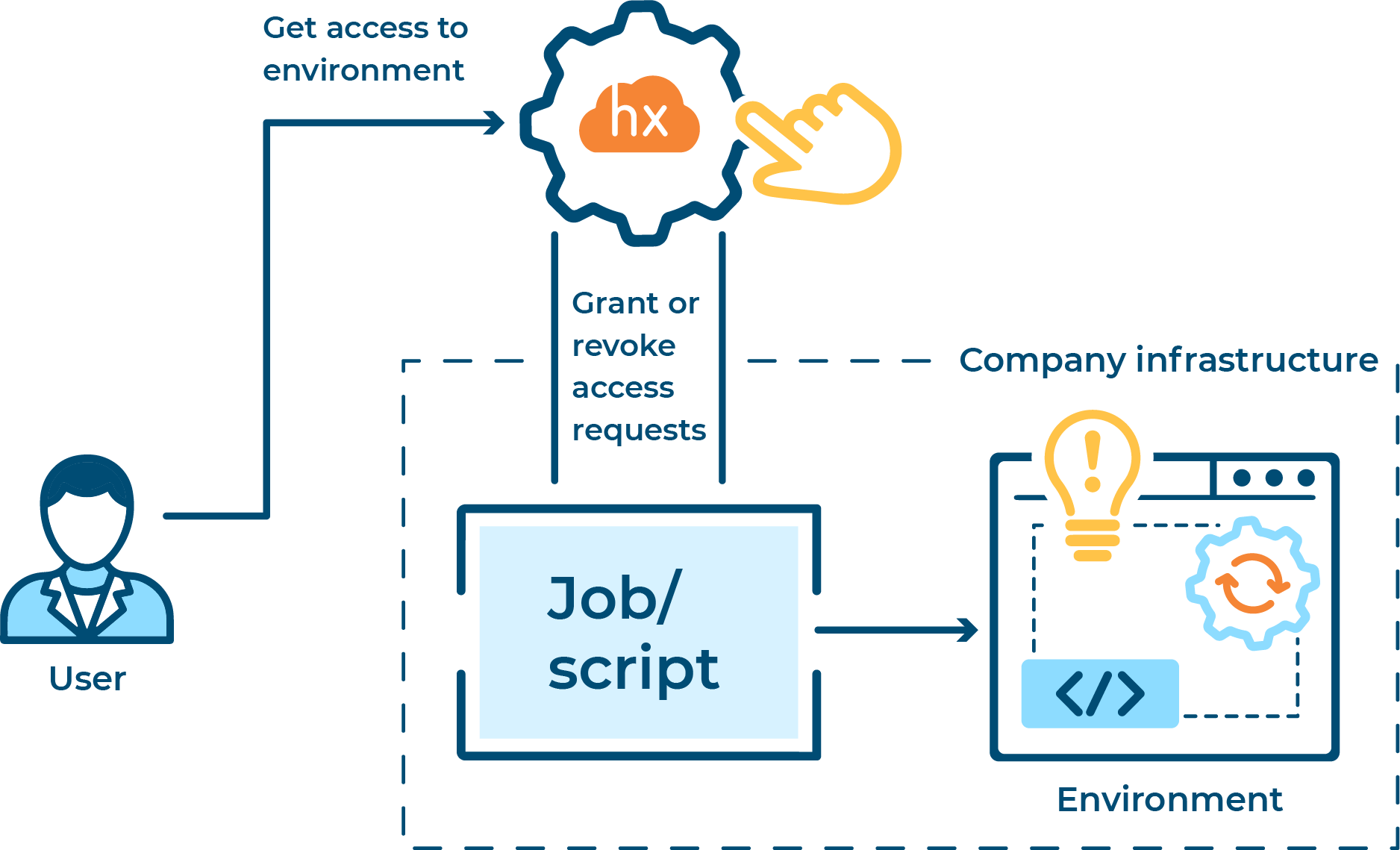
OptScale - FinOps
Descripción general de FinOps
Optimización de costos:
AWS
MS Azure
Nube de Google
Alibaba Cloud
Kubernetes
OptScale - MLOps
Perfiles de ML/IA
Optimización de ML/IA
Perfilado de Big Data
PRECIOS DE ESCALA OPTICA
Acura: migración a la nube
Descripción general
Cambio de plataforma de la base de datos
Migración a:
AWS
MS Azure
Nube de Google
Alibaba Cloud
VMware
OpenStack
KVM
Nube pública
Migración desde:
En la premisa
Acura — Recuperación ante desastres y copia de seguridad en la nube
Descripción general
Migración a:
AWS
MS Azure
Nube de Google
Alibaba Cloud
VMware
OpenStack
KVM